Introduction
Know Your Customer (KYC) is a critical component for businesses that need to verify user identities, ensure compliance with regulations, and prevent fraud. Implementing a robust KYC solution requires a mix of artificial intelligence (AI), machine learning (ML), and identity verification tools. This article outlines a step-by-step approach to building a KYC system that meets the following requirements & Summary of Steps : Technology Stack & Solution Components – You need a combination of AI/ML-powered identity verification tools, OCR for document scanning, deepfake detection algorithms, and a flexible admin dashboard.
Identity Verification API: Choose a provider that offers OCR, face recognition, and document verification. Examples: Jumio, Onfido, Sumsub, Veriff.
Rules Builder & Custom Parameters: Implement a flexible policy engine where admins can define risk rules based on geolocation, document type, or tax ID.
OCR Services: Use Tesseract OCR, Google Vision API, or AWS Textract for extracting details from ID documents and POA (Proof of Address).
Deepfake & AI Detection: Implement AI-powered liveness detection (e.g., FaceTec, ID R&D) to prevent synthetic identity fraud.
Forgery Check (ID & POA): Use AI-powered fraud detection tools that scan documents for tampering, modifications, and anomalies.
Non-doc Verifications: Biometric verification, phone/email verification, social security validation, or geolocation tracking.
Admin Dashboard: A React/Next.js frontend with a Node.js or Python backend, supporting manual review flow.
Manual Review Flow: If auto-verification fails, allow manual agents to review cases, annotate, and approve/reject.
Legacy Data Migration: Migrate existing user KYC data via ETL pipelines (Extract, Transform, Load).
Mobile SDK for KYC: Use React Native / Flutter SDKs for seamless mobile integration.
Age Verification: AI-powered face estimation or official document DOB extraction.
Step 1: Choose a KYC API Provider
The first step in implementing a KYC solution is selecting an API provider that offers robust identity verification capabilities. Some of the best providers in the market include:
|
|
|
Step 2: Develop a Rules Engine
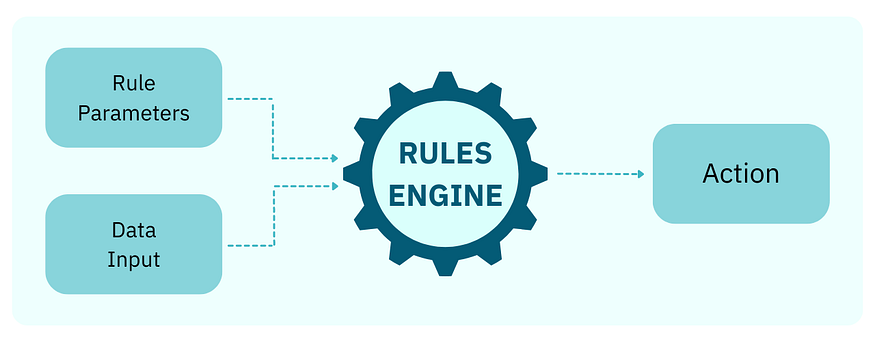
A rules engine is a core component of any KYC (Know Your Customer) system, allowing businesses to define, manage, and enforce verification policies dynamically. It ensures that user identity verification processes comply with internal risk policies, regulatory requirements, and fraud prevention measures.
Why is a Rules Engine Important?
Instead of hardcoding verification rules into the system, a rules engine provides the flexibility to adjust requirements dynamically without redeploying the software. This adaptability is crucial for keeping up with regulatory changes, such as varying KYC rules across different countries, responding to emerging fraud trends like new identity fraud patterns, and aligning with evolving business policies, such as stricter verification measures for high-risk users. A well-structured rules engine allows administrators to define conditions tailored to specific risks, such as requiring manual review for users from flagged high-risk countries, rejecting applications that lack a Tax ID in certain jurisdictions, or triggering additional verification steps if a document appears to be altered. This ensures a robust, compliant, and scalable identity verification process.
Key Features of a KYC Rules Engine
Dynamic Rule Configuration: Admins should be able to create, modify, and deactivate rules via an interface (no coding needed). Example: If a user uploads an expired ID, automatically reject it. | Conditional Logic & Custom Parameters: Rules should follow IF-THEN logic, e.g.: IF the document is from Country X, THEN require manual review. IF the Tax ID is missing, THEN reject the application. | Risk Scoring System: Assign risk scores based on multiple factors (e.g., document type, IP location, face match confidence). Example: A user with a low confidence score (<80%) may require video verification. | Integration with External Databases: Cross-check details against government databases, watchlists (OFAC, FATF), and fraud detection systems. | Automated Actions Based on Rules: Approve, flag for review, reject, or request additional documents based on the predefined rules. |
How to Implement a Rules Engine?
1. Define Rule Categories
Identity Verification Rules: Ensure name, DOB, and face match with documents.
Document Rules: Validate expiry dates, detect forgery, and check authenticity.
Tax ID Rules: Enforce submission where legally required.
Age Verification Rules: Auto-reject users under the minimum required age.
2. Choose a Technology for Implementation Depending on your stack, you can use:
Custom-built Rules Engine: Developed using Node.js, Python (Django/FastAPI), or Java with a database.
Open-source Rules Engines:
Drools (Java-based) – Good for enterprise-level logic.
nRules (.NET-based) – Flexible and scalable.
RuleJS (JavaScript) – Lightweight for frontend rule enforcement.
3. Build an Admin Dashboard for Rule Management– Admins should have a UI to define, test, and deploy rules dynamically.
Frontend: React.js or Angular.
Backend: Node.js, Python, or Java.
Database: PostgreSQL or MongoDB to store rules and their conditions.
4. Implement a Rule Execution Engine
Use a decision tree or if-else-based logic to check each rule against incoming data.
Store rules in a JSON format so they can be modified easily.
Example Rule in JSON

5. Automate Rule Enforcement
- Use AI and machine learning to improve rule effectiveness: Example: If an ID appears photoshopped, auto-flag it for review.
Implement real-time monitoring to track rule effectiveness and false positives. - Thoughts on rules engine: A well-designed KYC rules engine enhances security, automates identity verification, and ensures regulatory compliance without requiring frequent code changes. By implementing a dynamic and AI-assisted rules system, you can quickly adapt to evolving fraud techniques and compliance needs.
Would you like help designing the architecture for your specific business case? 🚀 Consult us
Step 3: Implement OCR and AI Fraud Detection
OCR (Optical Character Recognition) and AI-driven fraud detection are essential components of a modern KYC system. They work together to extract user details from identity documents and ensure that those documents are genuine, unaltered, and not fraudulent.
Why is OCR Important? OCR enables automated data extraction from identity documents such as passports, driver’s licenses, and utility bills. Instead of requiring manual data entry, OCR scans the document and converts text from images into structured data. This process speeds up verification, reduces human errors, and improves user experience.
How OCR Works in KYC? Image Processing: Enhances the document quality (e.g., removes noise, corrects skew).
Text Detection: Identifies text regions within the image.
Character Recognition: Converts detected text into machine-readable format.
Data Structuring: Extracted details (name, DOB, ID number) are mapped to corresponding fields.
 Technologies for OCR Processing:
Technologies for OCR Processing:
- AWS Textract: AI-powered OCR that can analyze complex documents and detect text, tables, and forms.
- Google Vision API: Cloud-based OCR with built-in support for passport and ID scanning.
- Tesseract OCR: Open-source OCR engine (best for on-premise solutions but requires additional preprocessing for high accuracy).
Why is AI Fraud Detection Necessary? OCR alone cannot detect document forgery—fraudsters can modify scanned documents using Photoshop, deepfake techniques, or even print manipulated copies. AI-powered fraud detection ensures the authenticity of the document by analyzing various factors such as:
- Tampering Detection: AI checks for pixel inconsistencies, altered fonts, and manipulated data fields.
- Hologram & Watermark Verification: AI scans for security features present in genuine IDs.
- Signature & Face Matching: AI verifies that the signature and profile photo match across different documents.
- Forgery Patterns: Machine learning models compare new documents against a database of known fraudulent documents.
Technologies for Fraud Detection:
- OpenCV: Detects image anomalies, blurriness, and color mismatches in documents.
- TensorFlow/PyTorch: Machine learning models trained to detect forged signatures and manipulated ID images.
- AWS Rekognition: AI-powered facial comparison and text anomaly detection to validate ID authenticity.
How OCR and AI Fraud Detection Work Together
- OCR scans the document and extracts text.
- analyzes the document for forgeries and alterations.
- Data validation checks (e.g., cross-referencing passport numbers with government databases).
- Risk scoring is applied (e.g., if a document is flagged as suspicious, a manual review is triggered).
By integrating OCR with AI-driven fraud detection, businesses can automate identity verification while preventing document manipulation and identity fraud. 🚀
Step 4: Integrate Deepfake & Liveness Detection
With the rise of AI-generated deepfakes and sophisticated identity fraud techniques, businesses need strong liveness detection and deepfake prevention in their KYC workflows. These technologies ensure that the person verifying their identity is a real, live human and not a digitally altered image, pre-recorded video, or AI-generated deepfake.
Why is Deepfake & Liveness Detection Important? Fraudsters often attempt to bypass KYC systems using:
❌ Pre-recorded videos (playing a video of the person instead of appearing live).
❌ Printed or digital images (holding up a picture of someone else to pass face recognition).
❌ AI-generated deepfakes (synthetic videos where an attacker’s face is swapped with someone else’s).
To combat these threats, AI-powered liveness detection ensures that the person interacting with the KYC system is physically present and exhibiting natural human movements.
What is Liveness Detection? Liveness detection verifies that a user is a real, live human and not a spoofed attempt. It does this by analyzing:
✅ Micro-movements (eye blinks, head tilts, slight facial expressions).
✅ Depth & 3D face structure (ensures a real face is in front of the camera, not a 2D image).
✅ Infrared & color analysis (detects inconsistencies in lighting that indicate screen-based attacks).
✅ Challenge-response tests (asks the user to perform random actions like smiling or turning their head).
What is Deepfake Detection? Deepfake detection uses AI to identify manipulated videos or synthetic faces. It scans for:
❌ Unnatural skin texture and lighting (AI-generated faces often have inconsistencies).
❌ Blinking & facial expression irregularities (deepfake models struggle with natural blinks and emotions).
❌ Frame-by-frame inconsistencies (video deepfakes may show minor glitches between frames).
❌ Lip-sync mismatches (voice and lip movements may be slightly out of sync).

Technologies for Liveness & Deepfake Detection
- FaceTec – 3D face liveness detection with AI-powered fraud prevention.
- iProov – Cloud-based biometric authentication that verifies real users and detects deepfakes.
- ID R&D – Passive liveness detection with AI-driven facial anti-spoofing.
- OpenCV + Deep Learning – Custom in-house liveness and deepfake detection models.
How to Implement Liveness & Deepfake Detection?
- Capture Live Face Data
- The system prompts the user to capture a selfie or short video.
- The AI models analyze head movement, blinking, and skin texture.
- Apply 3D Face Mapping & Depth Analysis
- A 3D depth map is created to ensure the user’s face has natural depth and shape.
- Technologies like Apple’s FaceID or WebRTC-based depth detection help detect 2D image frauds.
- Detect Deepfake Patterns
- AI scans the face for pixel inconsistencies, unnatural blinks, and visual distortions.
- Frame-by-frame analysis detects abnormalities in facial transitions.
- Challenge-Response Verification (Optional)
- The user may be asked to nod, blink, or smile to prove real presence.
- AI ensures the user’s response matches real-time movements.
Benefits of Liveness & Deepfake Detection in KYC
✅ Prevents impersonation fraud – Stops attackers from using stolen photos/videos.
✅ Enhances security – Ensures that only real users complete verification.
✅ Automates verification – Reduces manual review workload.
✅ Meets compliance – Helps businesses comply with AML (Anti-Money Laundering) and GDPR regulations.
By integrating AI-powered liveness and deepfake detection, businesses can effectively combat identity fraud while providing a seamless user experience.
Would you like to implement any of the above technologies? Get a consultation 🚀
Step 5: Develop the Admin Dashboard
The admin dashboard is a crucial part of the KYC system, providing a centralized platform for monitoring user verifications, configuring custom rules, managing risk scoring, and conducting manual reviews. It enables compliance officers and fraud analysts to efficiently handle KYC verification processes, detect fraudulent activity, and adjust system rules dynamically.
Why is an Admin Dashboard Important?
A well-designed admin dashboard enhances visibility, control, and decision-making for KYC processes. It helps businesses:
- Monitor User Verification Status – Track which users are approved, pending, or rejected.
- Configure & Update Rules – Adjust verification rules dynamically without changing code.
- Assess Risk & Fraud Patterns – Use risk scoring to identify suspicious users.
- Handle Manual Reviews – Allow staff to review flagged applications and take action.
Key Features of the KYC Admin Dashboard
| 1. User Verification Status Overview A dashboard displaying real-time verification progress for all users. Status indicators like:✅ Approved – Verified users. ⏳ Pending – Users under review. ❌ Rejected – Users with failed verification. ⚠️ Flagged for Review – Users requiring manual verification. | 2. Custom Rule Configurations An interactive rules builder to define risk policies dynamically. Example rules:”Reject users under 18″ “Require additional verification for high-risk countries” “Trigger manual review if Tax ID is missing” Implemented using a no-code or low-code interface for ease of modification. | 3. Risk Scoring System Assign a risk score (0-100) based on fraud detection and document authenticity. Factors influencing risk score:Document forgery detection Face match confidence level IP geolocation mismatch Duplicate applications detected Higher-risk users are flagged for additional verification. |
| 4. Manual Review Functionality Allows compliance officers to review flagged applications manually. Features: ✅ View uploaded ID documents and compare with extracted OCR data. ✅ Check AI-generated fraud detection alerts. ✅ Approve or reject applications with comments. | 5. Search & Filter Options Search users by name, ID, email, or verification status. Filter applications based on risk level, country, and verification method. | 6. Activity Logs & Audit Trail Logs all verification attempts, rule changes, and manual reviews for compliance tracking. Helps with regulatory audits and internal security checks. |
Technologies for the Admin Dashboard
Frontend: React.js
React.js provides a fast, responsive UI for displaying verification data.
Can integrate with UI frameworks like Material-UI or Ant Design for a polished look.
Backend: Node.js or Python
Node.js (Express.js) or Python (Django/FastAPI) for handling API requests.
Connects to databases storing user verification data, risk scores, and admin logs.
Database:
PostgreSQL (structured user data).
MongoDB (if handling unstructured KYC data like document images).
Elasticsearch (for fast search functionality).
How the Dashboard Works
- Admin logs in securely (OAuth, 2FA authentication).
- Dashboard loads real-time user verification data from the backend.
- Admins review flagged cases, approve or reject manually.
- Risk scoring algorithm updates users’ risk levels dynamically.
- Rule updates are applied instantly via the rules engine.
Benefits of a Well-Designed KYC Admin Dashboard
- Increases efficiency – Reduces manual review workload with automation.
- Improves fraud detection – Uses AI-powered risk scoring to highlight suspicious users.
- Enhances compliance – Provides full audit trails for regulatory purposes.
- Flexible & scalable – Allows dynamic rule modifications without code changes.
By integrating an AI-driven KYC admin dashboard, businesses can ensure faster, more accurate identity verification while maintaining compliance with regulations.
Would you like a dashboard UI wireframe or API integration guide? 🚀
Step 6: Implement Mobile SDK
A Mobile KYC SDK is a pre-built kit containing the necessary components for identity verification that clients can embed directly into their mobile applications. Instead of building their own KYC solution from scratch, businesses can integrate the SDK to handle document scanning, facial recognition, liveness detection, and fraud prevention within their app’s existing flow.
✅ Frictionless User Experience – Users can scan documents, verify their identity, and complete onboarding without switching to a desktop.
✅ Higher Completion Rates – Mobile-optimized verification increases user engagement and reduces drop-off rates.
✅ Advanced Security – Mobile devices support biometric authentication (Face ID, fingerprint), enhancing fraud prevention.
✅ Access to Device Hardware – Leverage camera, NFC, and sensors for accurate document scanning and liveness detection.
Step 7: Enable Legacy Data Migration
If your company already has a KYC database with verified users, it is crucial to migrate this data into the new system without disrupting operations. Legacy data migration ensures that previously verified customers do not have to go through the verification process again, improving user experience and maintaining compliance records.
To achieve this, we use an ETL (Extract, Transform, Load) pipeline, which ensures that data is:
✔ Extracted from the old system,
✔ Transformed into the required format,
✔ Loaded into the new KYC system
Challenges in KYC Data Migration
Data Format Inconsistencies – Legacy data might be stored in different structures (CSV, SQL databases, JSON, etc.).
Incomplete or Corrupted Data – Old records may have missing or outdated information.
Compliance Requirements – Migrated data must meet current KYC/AML regulations.
Large Data Volumes – Millions of records may need to be moved without downtime
How to Implement KYC Data Migration?
Step 7.1: Assess Legacy Data Sources: Before migrating, analyze the existing database to understand: Example:
| Step 7.2: Extract Data from Legacy System: Use ETL tools or custom scripts to pull data from the old database. Technologies for Extraction: 🔹 Python scripts – Custom scripts to extract and preprocess data. |
Step 7.3: Transform Data to Match New System Requirements: Once extracted, the data needs to be cleaned and formatted to match the new KYC system’s structure. Key Transformation Steps: ✔ Normalize Date Formats – Convert | Step 7.4: Load Data into the New KYC System: Once the data is cleaned, it needs to be uploaded to the new KYC platform while preserving verification status. Technologies for Loading: 🔹 Database Import – Directly insert data into the new SQL or NoSQL database. |
Best Practices for KYC Data Migration
✔ Perform Data Validation – Check for missing fields and inconsistencies before importing.
✔ Ensure Data Security – Encrypt sensitive data during transfer.
✔ Run Test Migrations – Migrate a small sample of data before full migration.
✔ Maintain Backups – Keep a backup of the legacy database in case rollback is needed.
✔ Schedule Downtime (if required) – If real-time migration is not possible, plan a low-traffic window for the migration.
Migrating legacy KYC data is a critical step in ensuring a seamless transition to a new identity verification system. By implementing an ETL pipeline with modern data extraction, transformation, and loading tools, businesses can ensure compliance, security, and efficiency.
Would you like a custom ETL script or a step-by-step migration plan for your business? Let’s talk! 🚀
Step 8: Test and Deploy
Before going live, conduct security testing and ensure regulatory compliance.
Considerations:
- Penetration Testing – Identify security vulnerabilities
- Compliance Checks – Ensure GDPR, SOC2, and AML/KYC compliance
- Load Testing – Assess system performance under peak loads
Conclusion
Building a robust KYC system requires a mix of AI-driven identity verification, fraud prevention, and compliance mechanisms. By following this step-by-step guide, your company can ensure secure and efficient customer verification. Whether you opt for third-party KYC providers or build an in-house solution, the right approach will enhance security, reduce fraud, and streamline the user onboarding process.
Tech Stack Overview
| Feature | Technology |
|---|---|
| Identity Verification | Jumio, Onfido, Sumsub, Veriff |
| OCR Processing | Tesseract OCR, AWS Textract, Google Vision API |
| Deepfake & AI Detection | FaceTec, iProov, ID R&D |
| Rules Engine | Node.js + MongoDB / Python + PostgreSQL |
| Fraud Detection | OpenCV, TensorFlow, AWS Rekognition |
| Admin Dashboard | React.js + Node.js/Python |
| Mobile SDK | React Native, Flutter |
| Legacy Data Migration | Python ETL, AWS Glue, Apache NiFi |
Ready to Implement a Secure KYC Solution?
Ensure compliance, prevent fraud, and streamline identity verification with a custom-built KYC system. Hire an expert developer to design and integrate the perfect solution for your business.





